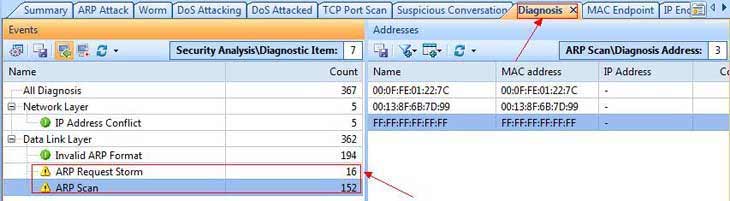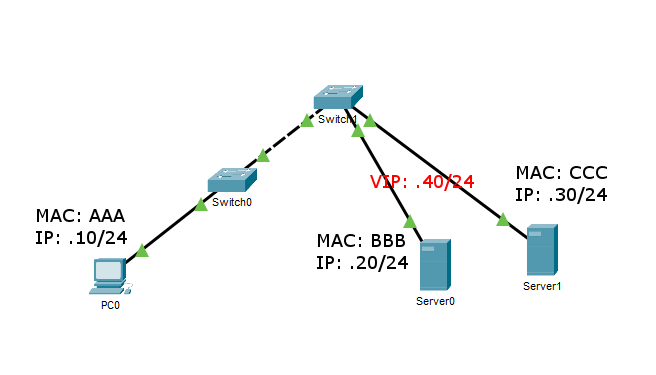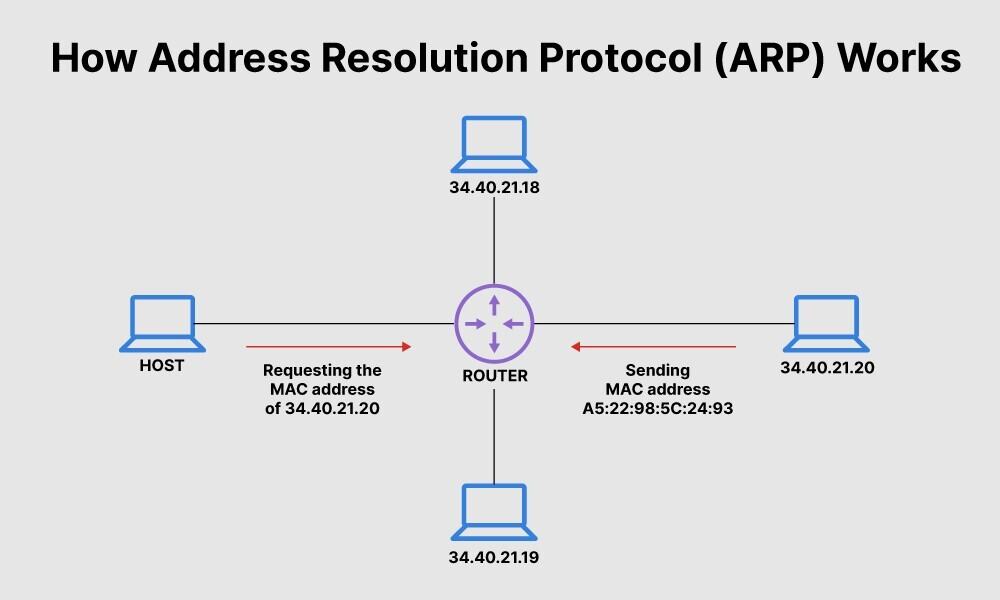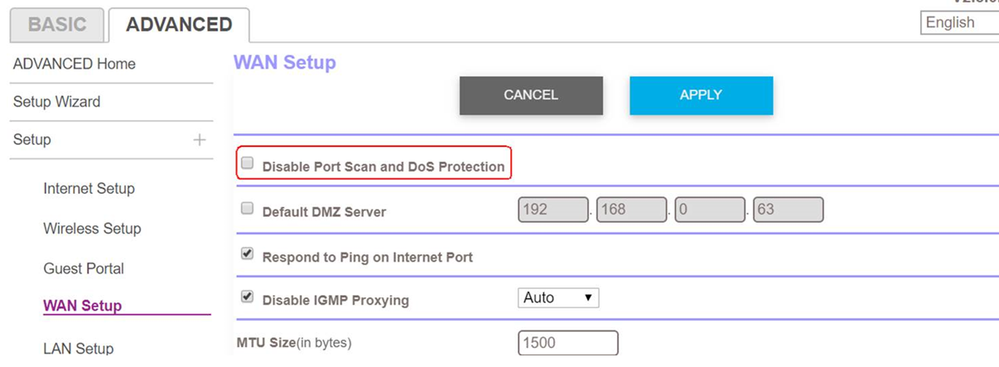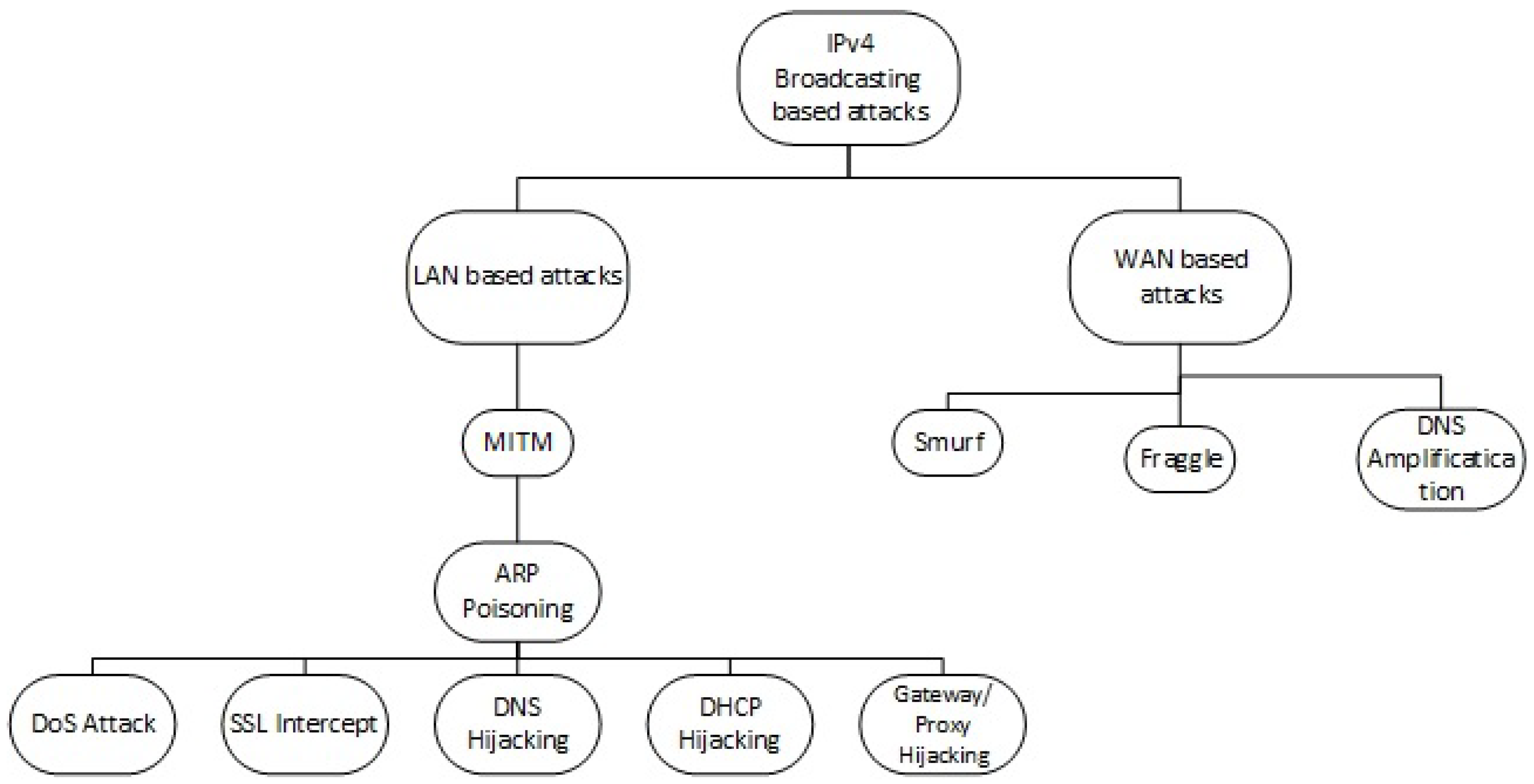
Electronics | Free Full-Text | PrECast: An Efficient Crypto-Free Solution for Broadcast-Based Attacks in IPv4 Networks | HTML

An analysis of security solutions for ARP poisoning attacks and its effects on medical computing | SpringerLink
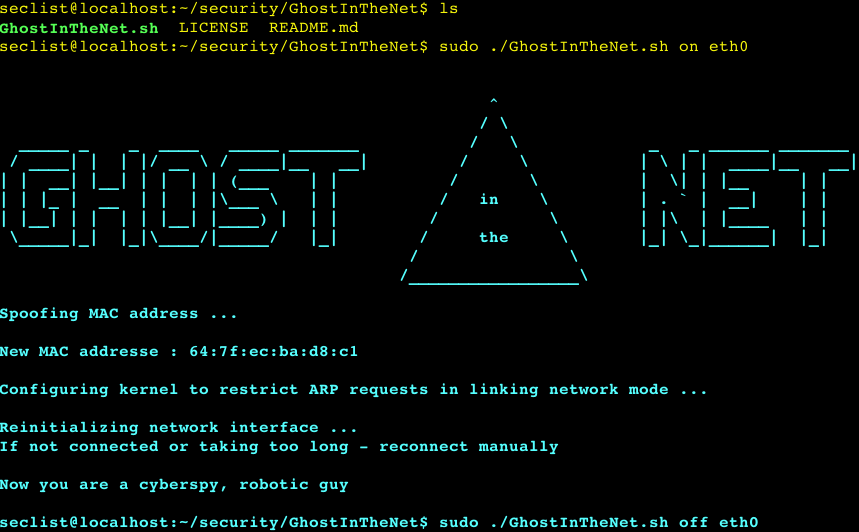
GhostInTheNet - Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan – PentestTools

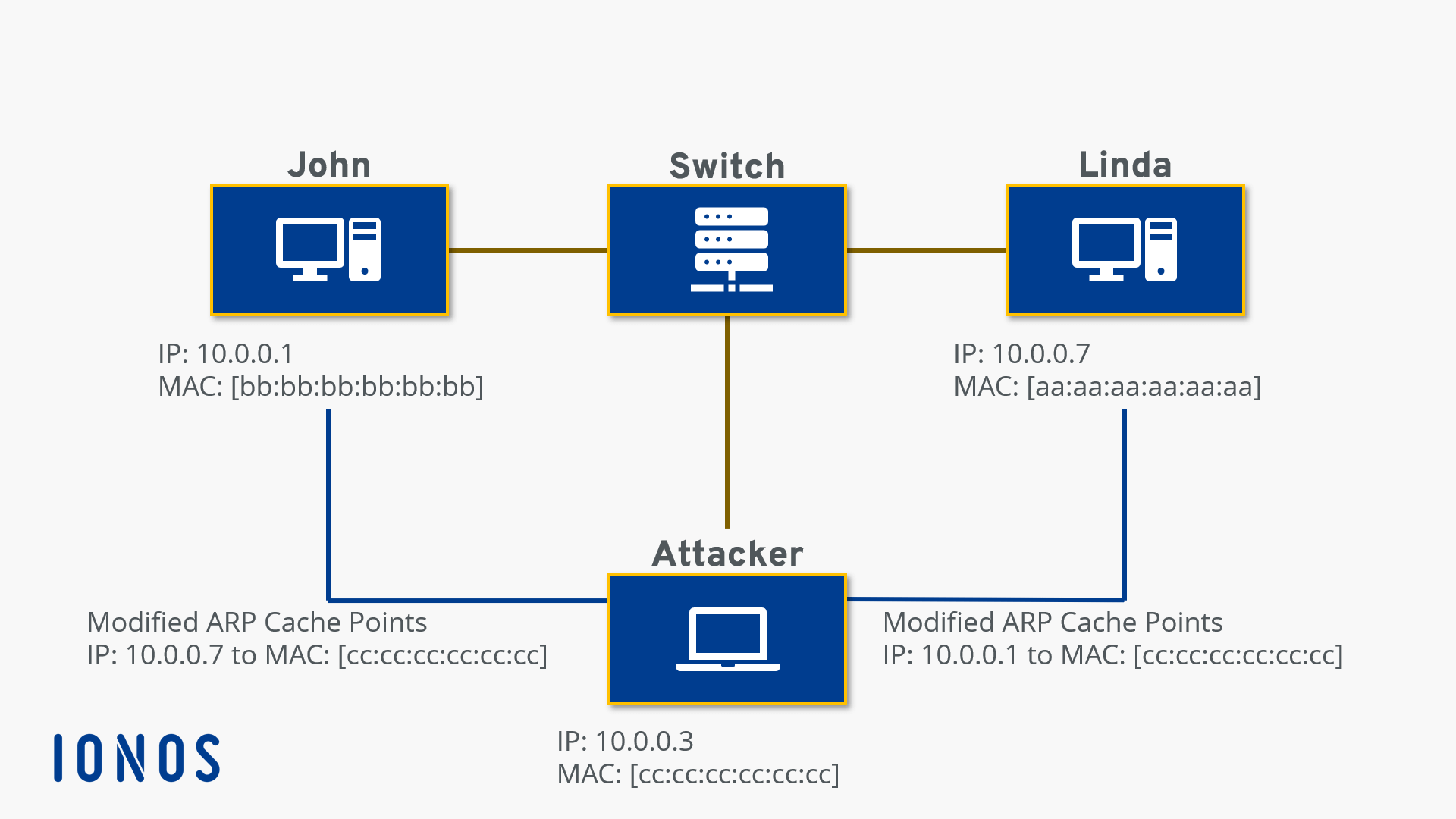


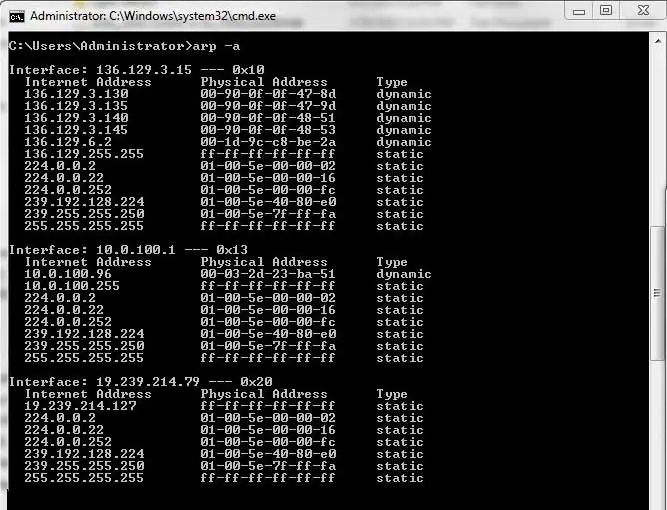


![Tutorial on ARP - Command-Line Tool to View and Manage your ARP Cache [Examples] Tutorial on ARP - Command-Line Tool to View and Manage your ARP Cache [Examples]](https://www.meridianoutpost.com/resources/articles/command-line/images/arp-s.png)