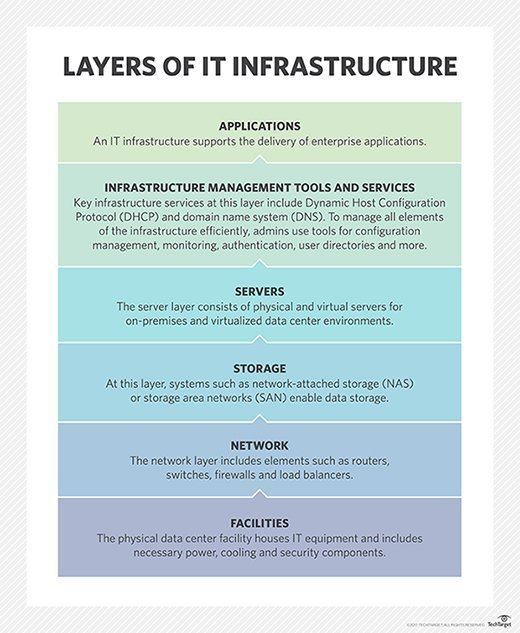
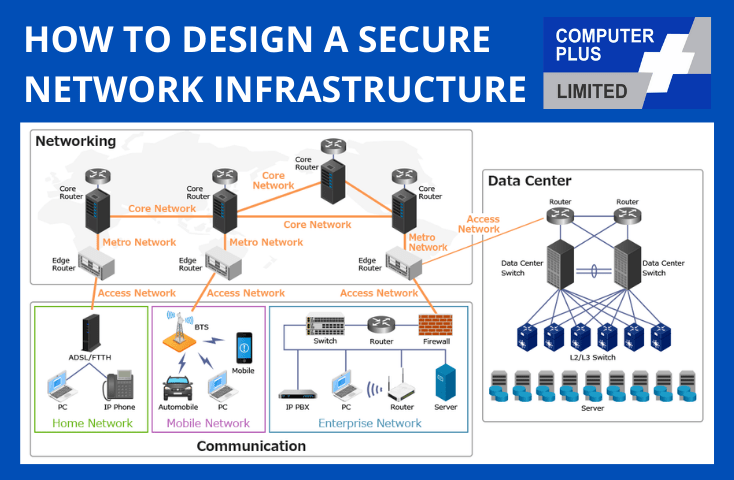
Skyscrapers illustration, IT infrastructure Security service Application security, INFRASTRUCTURE, computer Network, company, service png | PNGWing

Protect Your Business' IT Infrastructure: 7 Best Practices - COBAIT | Expert IT Consulting | IT Solutions | IT Services
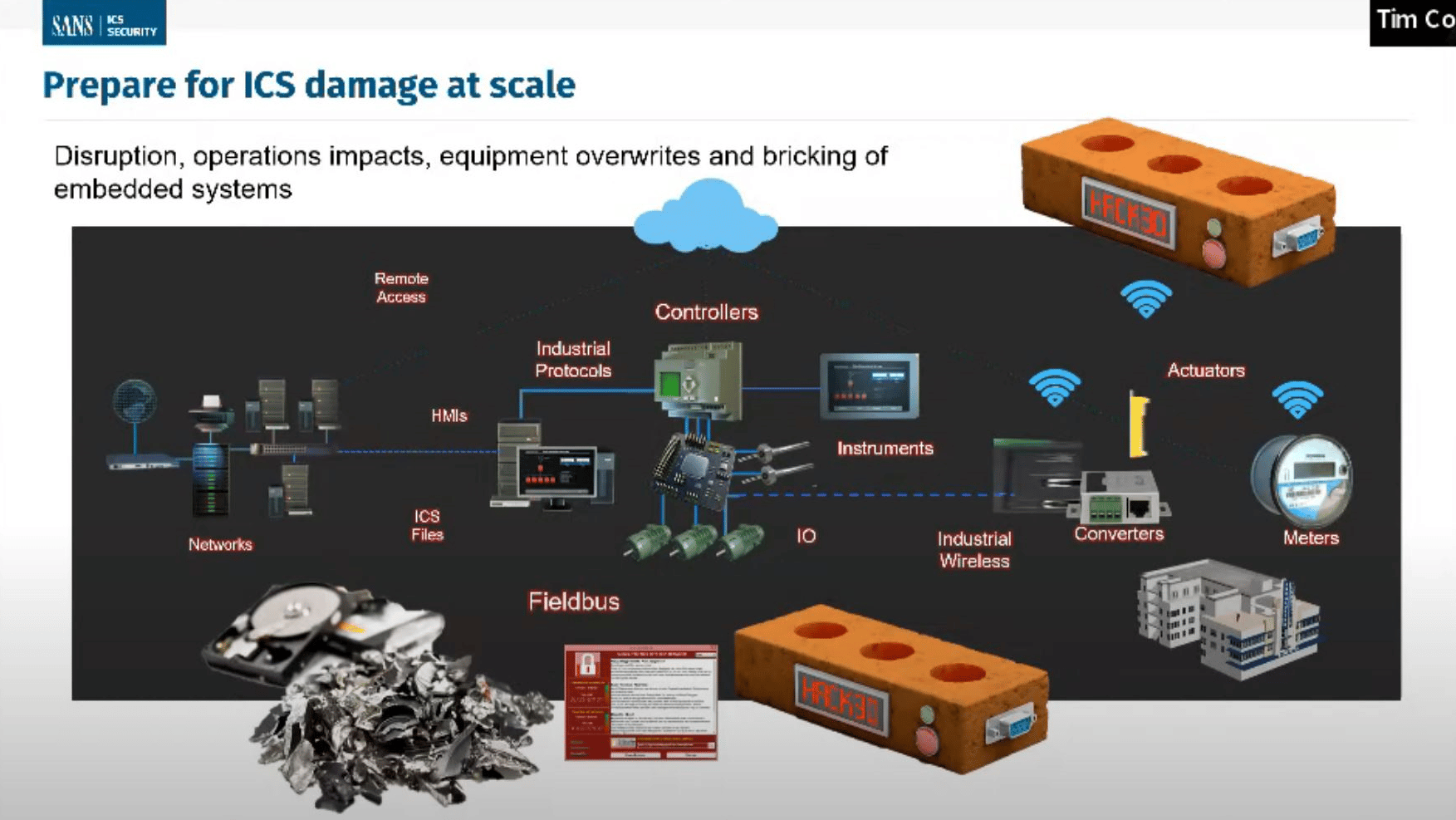
SANS Outlines Critical Infrastructure Security Steps as Russia, U.S. Trade Cyberthreats | eSecurityPlanet

Introducing the Cybersecurity and Infrastructure Security Agency - Homeland Security Digital Library