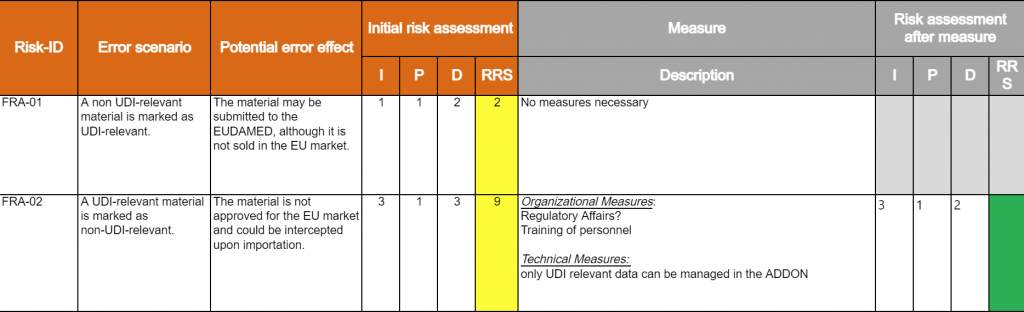
![E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book] E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book]](https://www.oreilly.com/library/view/information-assurance-handbook/9780071821650/t0383-01.jpg)
E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book]

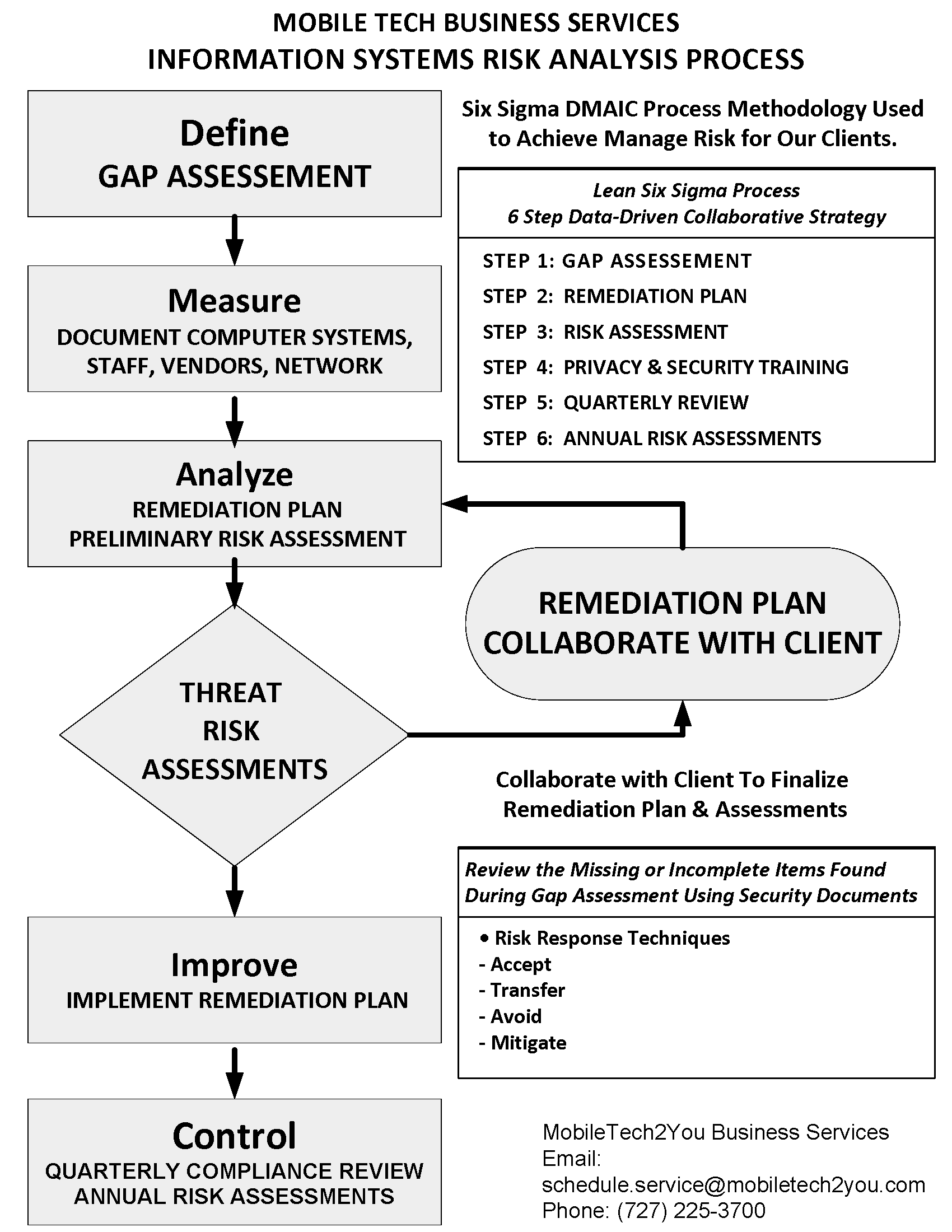
Cybersecurity for Executives: Advancing Leaders to Practical Cyber Risk Management: 9798887043135: Computer Science Books @ Amazon.com

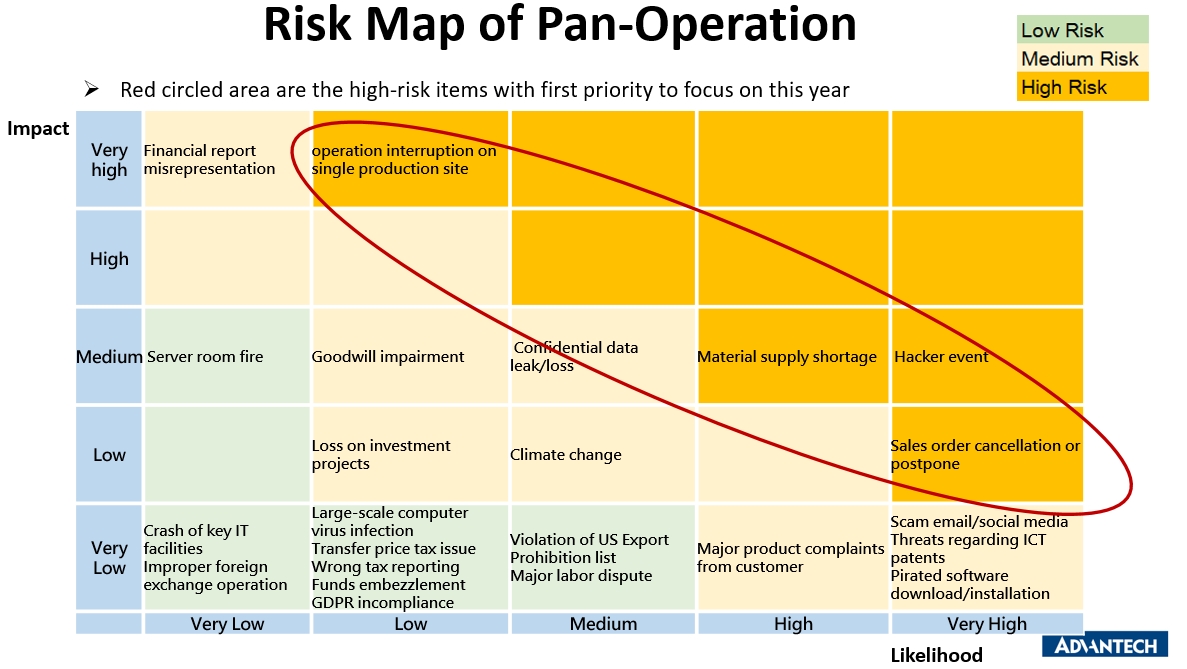
Risk assessment Risk management plan Computer Software Safety, risk analysis, infographic, template png | PNGEgg
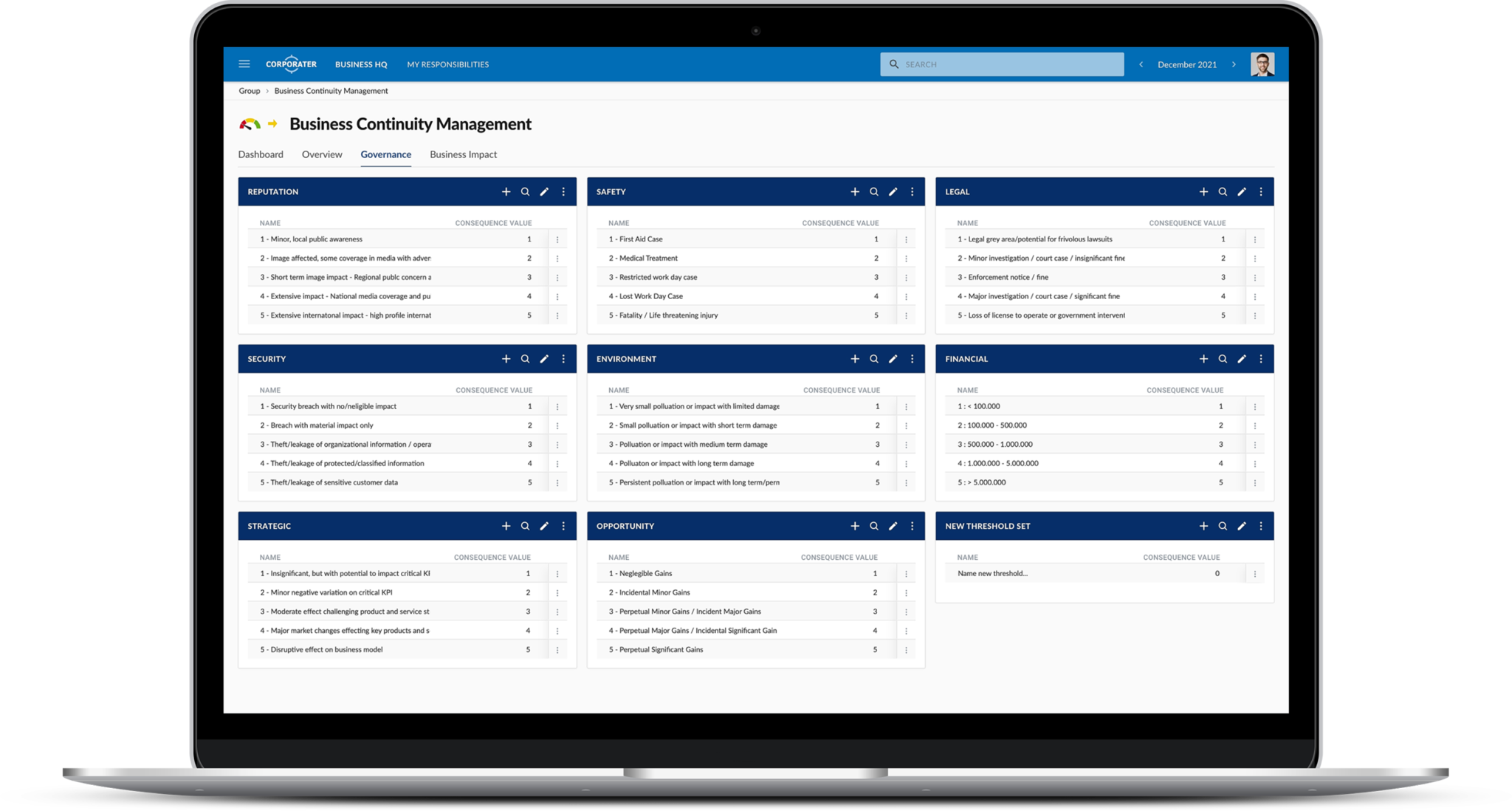
![E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book] E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book]](https://www.oreilly.com/library/view/information-assurance-handbook/9780071821650/t0384-01.jpg)
E Sample Risk Analysis Table - Information Assurance Handbook: Effective Computer Security and Risk Management Strategies [Book]