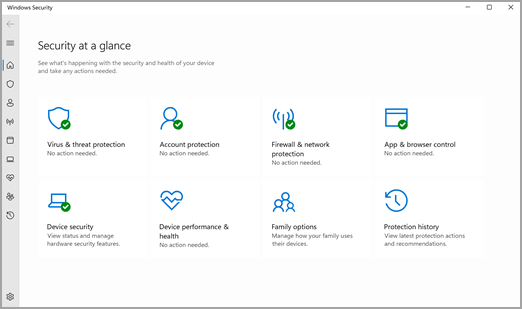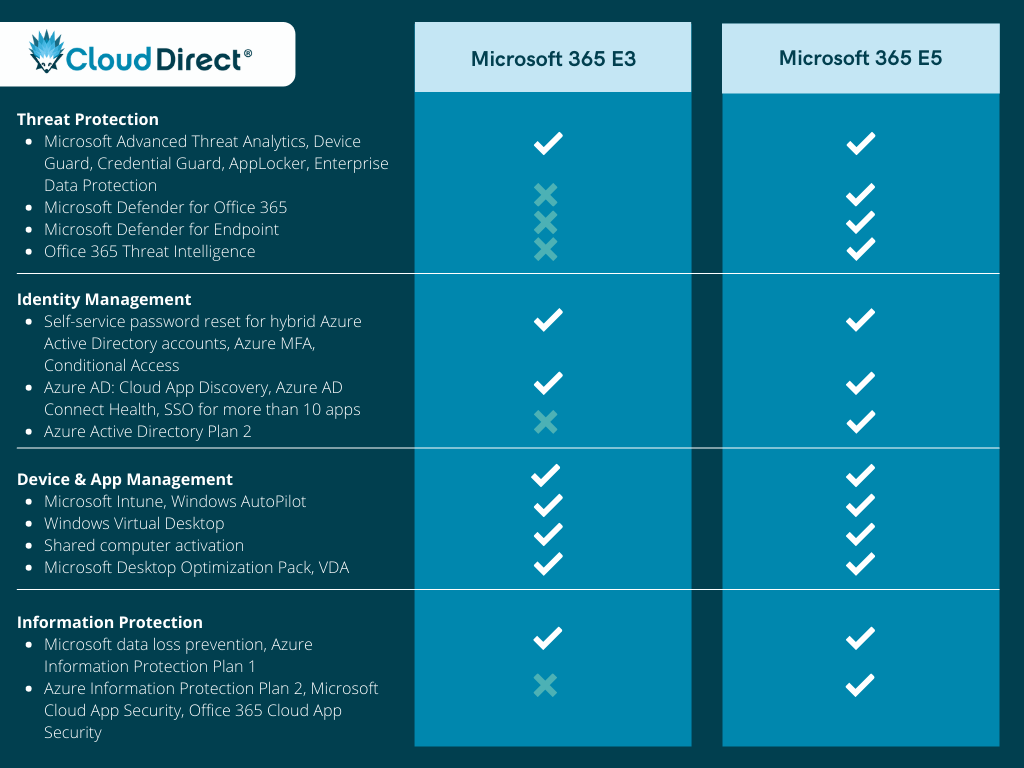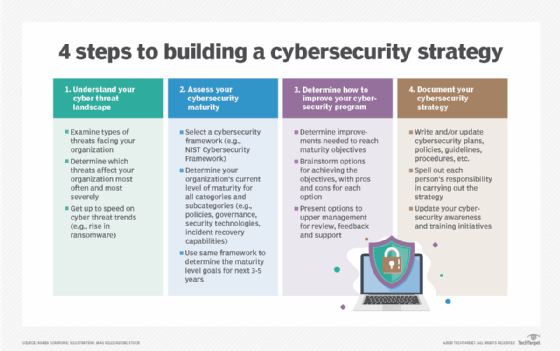
Cyber Security Module Features For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Course system of Internet of things engineering with security features | Download Scientific Diagram

Features of Microsoft's Cloud Computing Technology - Multisoft Virtual Academy - Blog | Cloud computing technology, Cloud computing, Cyber security awareness