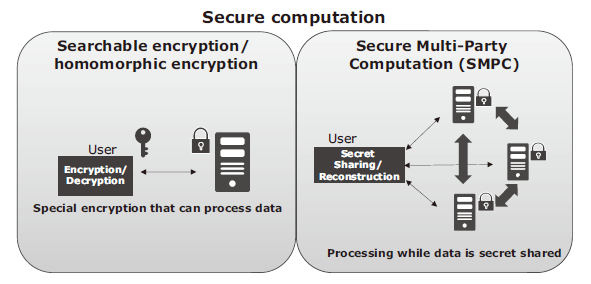
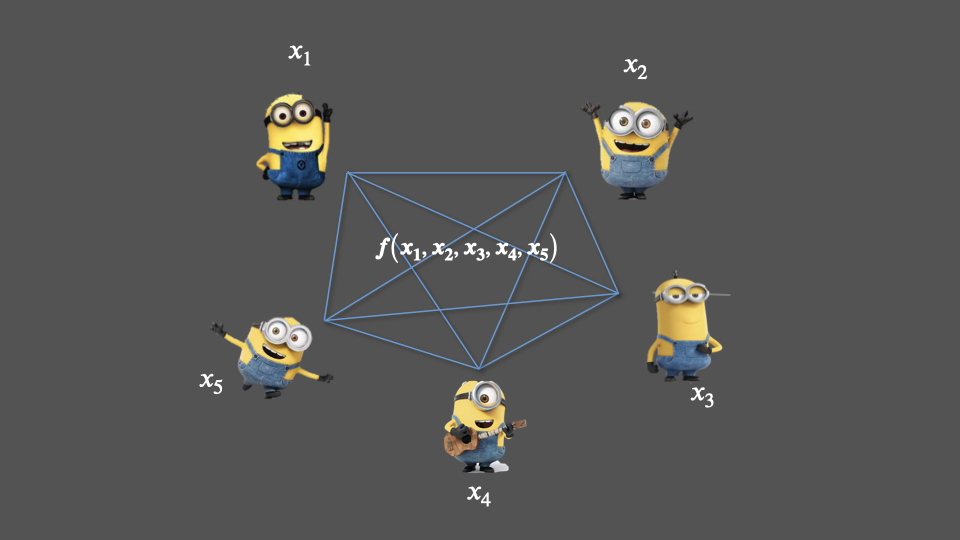
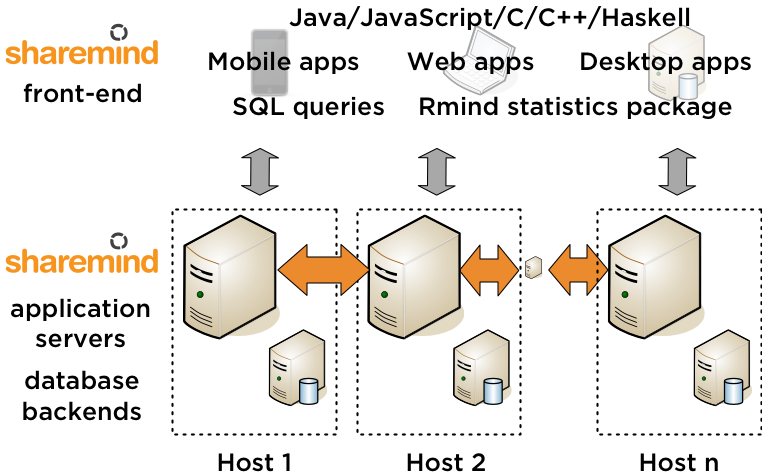
Secure multi-party computation: Each participant shares a separate,... | Download Scientific Diagram
Secure Multiparty Computation and Shamir's Secret Sharing on Wanchain | by Oliver Birch | Wanchain | Medium

A Secure Multi-Party Computation Protocol Suite Inspired by Shamir's Secret Sharing Scheme | Semantic Scholar

Multi-party Computation Alliance founded for digital privacy, security - Ledger Insights - blockchain for enterprise
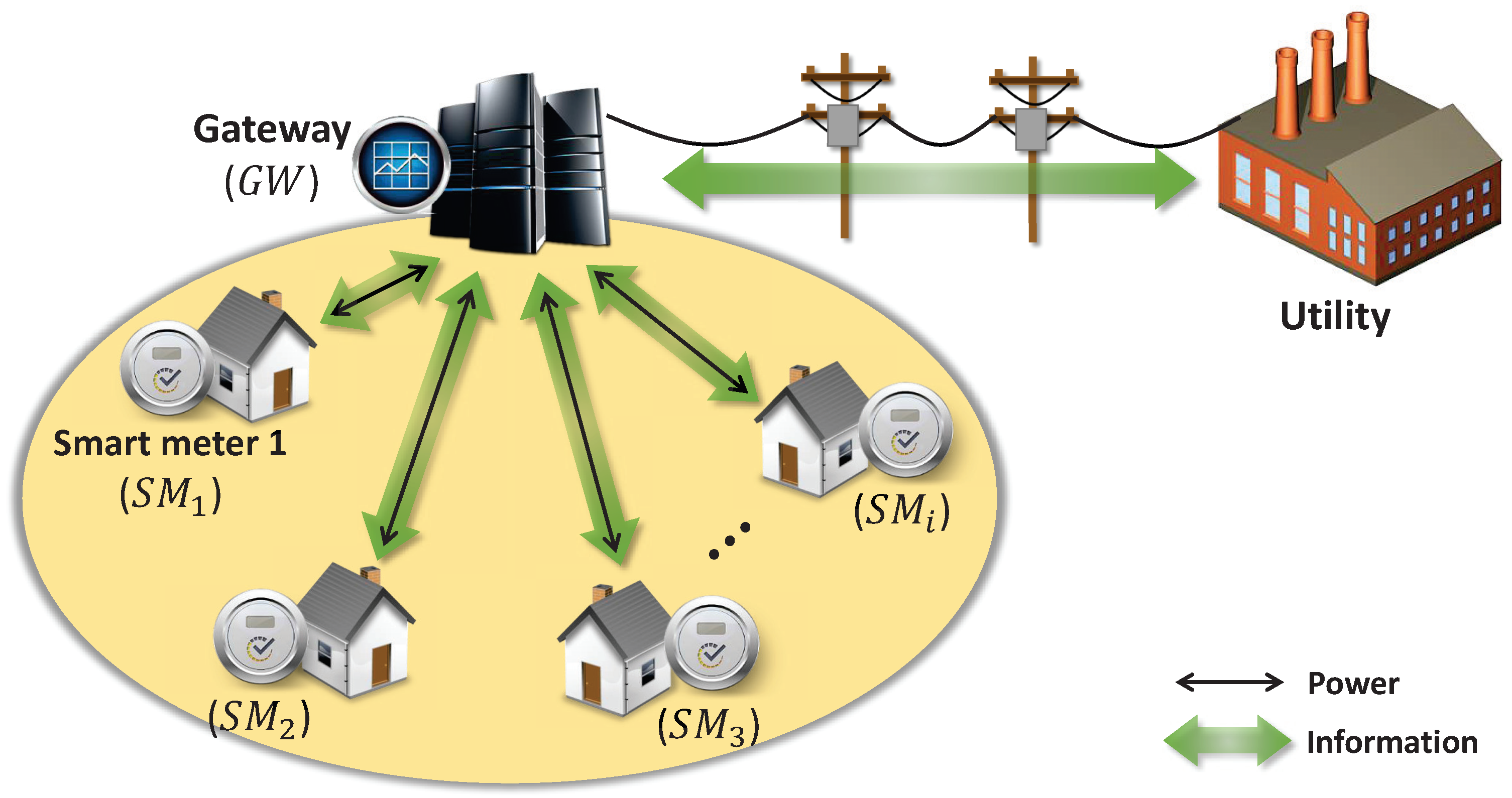
Cryptography | Free Full-Text | Fair and Secure Multi-Party Computation with Cheater Detection | HTML