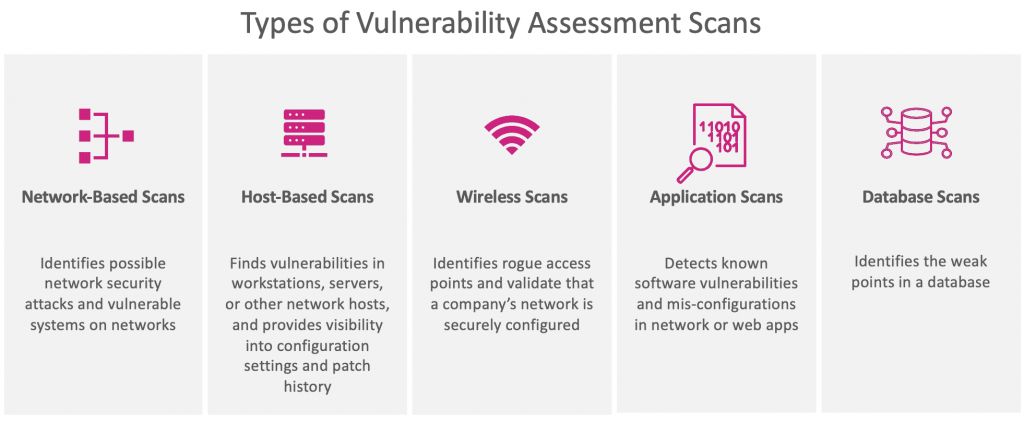
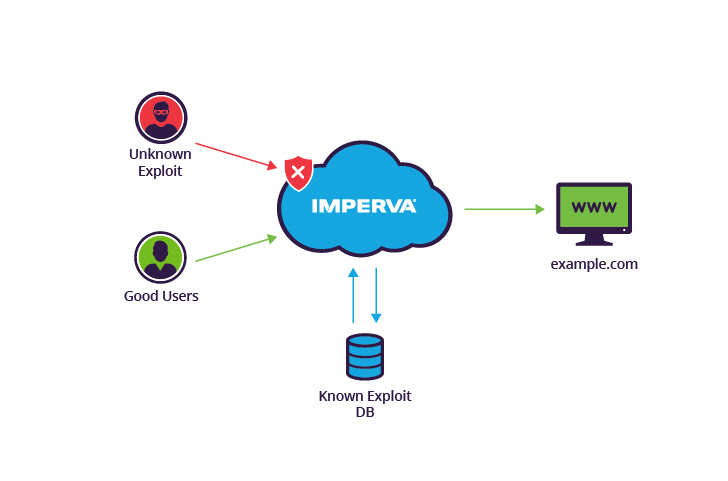
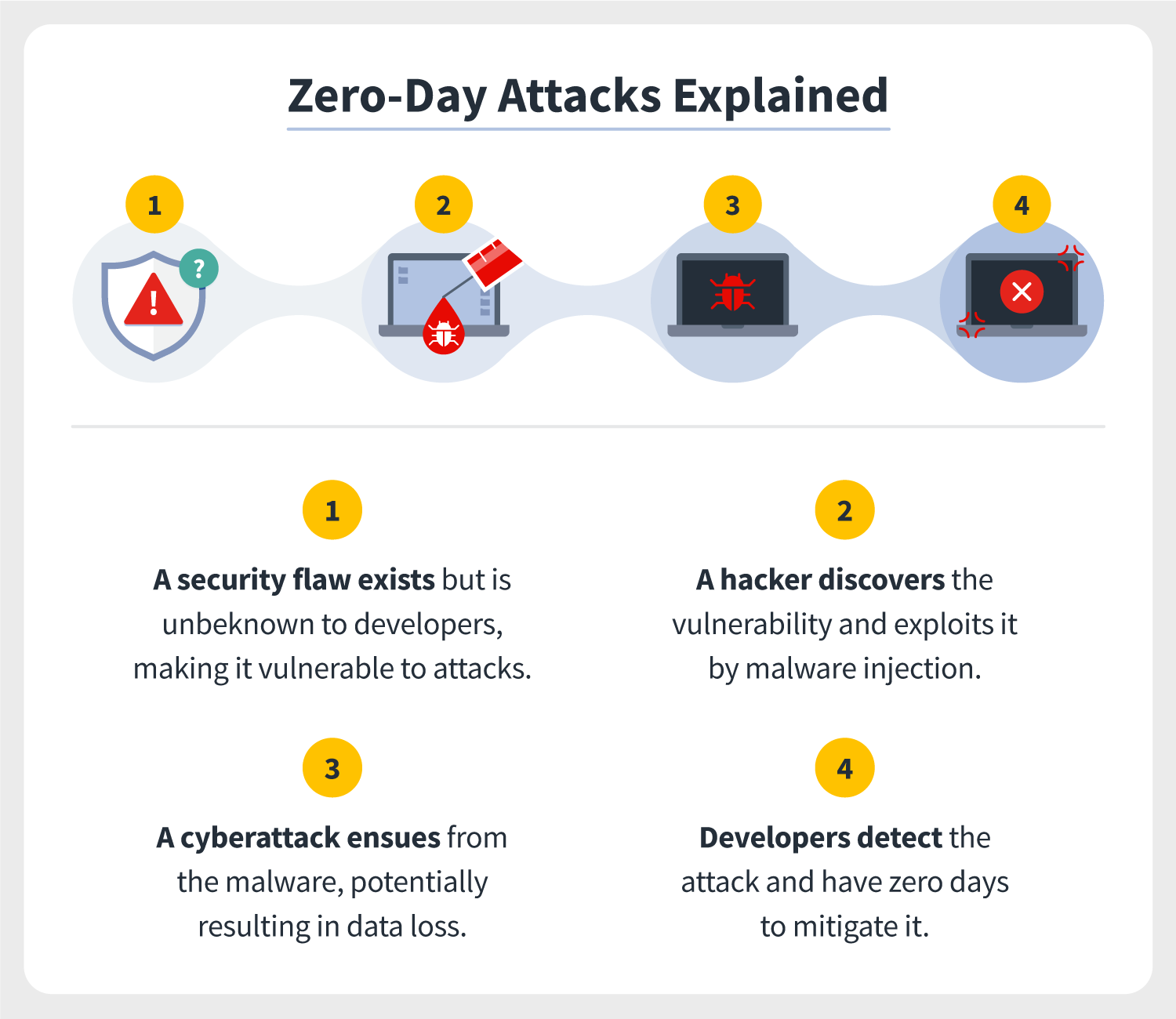
What Is a Security Vulnerability? Definition, Types, and Best Practices for Prevention | Spiceworks 1

What Is Vulnerability Assessment? Chapter 23. vulnerability In computer security, the term vulnerability is applied to a weakness in a system that allows. - ppt download